What is IP Adress?
An IP address is a fascinating product of modern computer technology designed to allow one computer (or other digital device) to communicate with another via the Internet. IP addresses allow the location of literally billions of digital devices that are connected to the Internet to be pinpointed and differentiated from other devices. In the same sense that someone needs your mailing address to send you a letter, a remote computer needs your IP address to communicate with your computer.
“IP” stands for Internet Protocol, so an IP address is an Internet Protocol address. What does that mean? An Internet Protocol is a set of rules that govern Internet activity and facilitate completion of a variety of actions on the World Wide Web. Therefore an Internet Protocol address is part of the systematically laid out interconnected grid that governs online communication by identifying both initiating devices and various Internet destinations, thereby making two-way communication possible.
An IP address consists of four numbers, each of which contains one to three digits, with a single dot (.) separating each number or set of digits. Each of the four numbers can range from 0 to 255. Here’s an example of what an IP address might look like: 78.125.0.209. This innocuous-looking group of four numbers is the key that empowers you and me to send and retrieve data over our Internet connections, ensuring that our messages, as well as our requests for data and the data we’ve requested, will reach their correct Internet destinations. Without this numeric protocol, sending and receiving data over the World Wide Web would be impossible.
IP addresses can be either static or dynamic. Static IP addresses never change. They serve as a permanent Internet address and provide a simple and reliable way for remote computers to contact you. Static IP addresses reveal such information as the continent, country, region, and city in which a computer is located; the ISP (Internet Service Provider) that services that particular computer; and such technical information as the precise latitude and longitude of the country, as well as the locale, of the computer. Many websites provide IP address look-up services to their visitors, free of charge. If you’re curious about your own IP address, you can locate these websites by performing a Google search.
Dynamic IP addresses are temporary and are assigned each time a computer accesses the Internet. They are, in effect, borrowed from a pool of IP addresses that are shared among various computers. Since a limited number of static IP addresses are available, many ISPs reserve a portion of their assigned addresses for sharing among their subscribers in this way. This lowers costs and allows them to service far more subscribers than they otherwise could.
Static IP addresses are generally preferable for such uses as VOIP (Voice over Internet Protocol), online gaming, or any other purpose where users need to make it easy for other computers to locate and connect to them. Easy access can also be facilitated when using a dynamic IP address through the use of a dynamic DNS service, which enables other computers to find you even though you may be using a temporary, one-time IP address. This often entails an extra charge, however, so check with your ISP.
Static IP addresses are considered somewhat less secure than dynamic IP addresses, since they are easier to track for data mining purposes. However, following safe Internet practices can help mitigate this potential problem and keep your computer secure no matter what type of IP address you use.
from : http://whatismyipaddress.com/ip-address/
What is Cat 5 cable?
 Short for Category 5, network cabling that consists of four twisted pairs of copper wire terminated by RJ45 connectors. Cat-5 cabling supports frequencies up to 100 MHz and speeds up to 1000 Mbps. It can be used for ATM, token ring, 1000Base-T, 100Base-T, and 10Base-T networking.
Short for Category 5, network cabling that consists of four twisted pairs of copper wire terminated by RJ45 connectors. Cat-5 cabling supports frequencies up to 100 MHz and speeds up to 1000 Mbps. It can be used for ATM, token ring, 1000Base-T, 100Base-T, and 10Base-T networking.
Computers hooked up to LAN s are connected using Cat-5 cables, so if you’re on a LAN, most likely the cable running out of the back of your PC is Category 5.
What is a Network Switch?
 To understand basic networking, you first need to answer the question, “What is a network switch?”
To understand basic networking, you first need to answer the question, “What is a network switch?”
Most business networks today use switches to connect computers, printers and servers within a building or campus. A switch serves as a controller, enabling networked devices to talk to each other efficiently. Through information sharing and resource allocation, switches save businesses money and increase employee productivity.
What is a Network Switch: Unmanaged Switches
An unmanaged switch works right out of the box. It’s not designed to be configured, so you don’t have to worry about installing or setting it up correctly. Unmanaged switches have less network capacity than managed switches. You’ll usually find unmanaged switches in home networking equipment.
What is a Network Switch: Managed Switches
A managed network switch is configurable, offering greater flexibility and capacity than an unmanaged switch. You can monitor and adjust a managed switch locally or remotely, to give you greater network control.
What is a Network Switch versus a Router?
Switches create a network. Routers connect networks. A router links computers to the Internet, so users can share the connection. A router acts as a dispatcher, choosing the best path for information to travel so it’s received quickly.
What is Hard Disk (HDD)
The hard disk drive (HDD) is the main, and usually largest, data storage device in a computer. The operating system, software titles and most other files are stored in the hard disk drive.
The Hard Disk Drive is Also Known As:
HDD (abbreviation), hard drive, hard disk, fixed drive, fixed disk, fixed disk drive
From : http://pcsupport.about.com/od/componentprofiles/p/p_hdd.htm
What is Firewall?
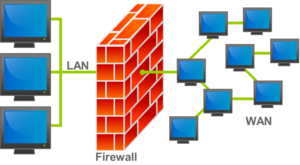 A firewall can either be software-based or hardware-based and is used to help keep a network secure. Its primary objective is to control the incoming and outgoing network traffic by analyzing the data packets and determining whether it should be allowed through or not, based on a predetermined rule set. A network’s firewall builds a bridge between an internal network that is assumed to be secure and trusted, and another network, usually an external (inter)network, such as the Internet, that is not assumed to be secure and trusted
A firewall can either be software-based or hardware-based and is used to help keep a network secure. Its primary objective is to control the incoming and outgoing network traffic by analyzing the data packets and determining whether it should be allowed through or not, based on a predetermined rule set. A network’s firewall builds a bridge between an internal network that is assumed to be secure and trusted, and another network, usually an external (inter)network, such as the Internet, that is not assumed to be secure and trusted


